SAML Bearer Assertion Flow in Office 365,Graph API with ADFS-2
In the previous post, we looked into the high level approach of fetching an OAuth token to get data from Graph API based on SAML assertion. Now let us understand on how we can actually fetch SAML Asserstion.
OAuth 2.0 SAML Bearer Assertion Flow
The OAuth 2.0 SAML bearer assertion flow defines how a SAML assertion is used to request an OAuth access token. A SAML assertion is an XML security token issued by an identity provider and consumed by a service provider. The service provider relies on its content to identify the assertion’s subject for security-related purposes.Pre-Requisites
- There is a trust relationship between the authorization server/environment- O365 and the issuer of the SAML 2.0 bearer assertion, which is the identity provider - ADFS. To configure ADFS for SSO and IDP you may refer to this article
- The application is registered in the office portal with below necessary configurations.Since we are using OAuth V2.0 endpoint,so need to register the application in App registration portal. Below are the steps
- Login to the App registration portal (Please note that we are using the v2.0 endpoints for Graph API and hence need to register the application in this portal. Otherwise we could have used the registrations in Azure active directory)
- Click "Add an App"
- Enter an "Application Name"
- Make a note of the Application id (this is referred as client id when required by the application)
- Click "Generate New Password" under Application secrets section. Please note that this will be flashed only once in the screen and make sure you note and save it in a safe place 😀
- Under section "Microsoft Graph Permissions", add delegated permission for "Tasks.read" since we intend to use the Outlook graph api.
- Click Save for saving the Application related settings and data.
- Postman Tool is required to test the Sample requests in three parts
Process to fetch the OAuth Token and Access Graph API
This can be achieved with the POSTMAN tool for POC in three parts as below. The same can be converted to code in any platform of your choice.
- Get the SAML assertion from ADFS
- Get the OAuth2 token using the assertion
- Get the data with the Oauth token
Get the SAML assertion from ADFS
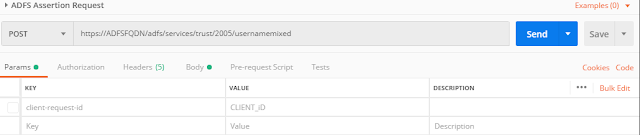
1. Create a POST request to ADFS endpoint with
SOAP envelope to fetch the SAML assertion
2. Header values as below
3. ADFS request body
Note : At the end of the post , i have attached the postman export files for reference
Once,this
request is posted successfully, you should receive a SAML Assertion from ADFS Only the <SAML:Assertion> tag data is required
for further requests
Convert the same to base64 encoding to use in
further requests.
Get the OAuth2 token using the assertion
In this step ,we will fetch a OAuth2 token using the ADFS assertion response.
1. Create a POST request as shown below with the header values.
2. In the Body of the request please do the following
Replace client_id, client_secret and
assertion (base 64 encoded SAML assertion obtained in step #1)
3. Upon successful request you will receive a access token from Azure active directory.
Get the data with the Oauth token
1. For the POC we will call
Graph API’s (e.g outlook tasks in this
example)
Create a GET request as shown below with the access token fetched in the earlier step.
2. Upon successful request , you will receive a json response.
I would say, there is much more to Azure but i did not find enough documentation to this topic. So for the benefit of the community, I tried jotting down the thoughts. Hope this helps !
I would say, there is much more to Azure but i did not find enough documentation to this topic. So for the benefit of the community, I tried jotting down the thoughts. Hope this helps !






I am getting error as AADSTS50107: Requested federation realm object does not exists even with the the assertion token in request body
ReplyDeleteGetting the same error as amarnath, but this is an old post so not surprising.
ReplyDelete